Setting up Delegated Authentication with SAML on Microsoft Azure
Before setting up the installer, you have to configure Microsoft Entra ID.
Set up Microsoft Entra ID
With an account with enough rights, go to : Enterprise Applications
- Click on
New Application - Click on
Create your own applicationon the top left corner - Choose a name for it, and select
Integrate any other application you don't find in the gallery - Click on "Create"
- Select
Set up single sign on - Select
SAML -
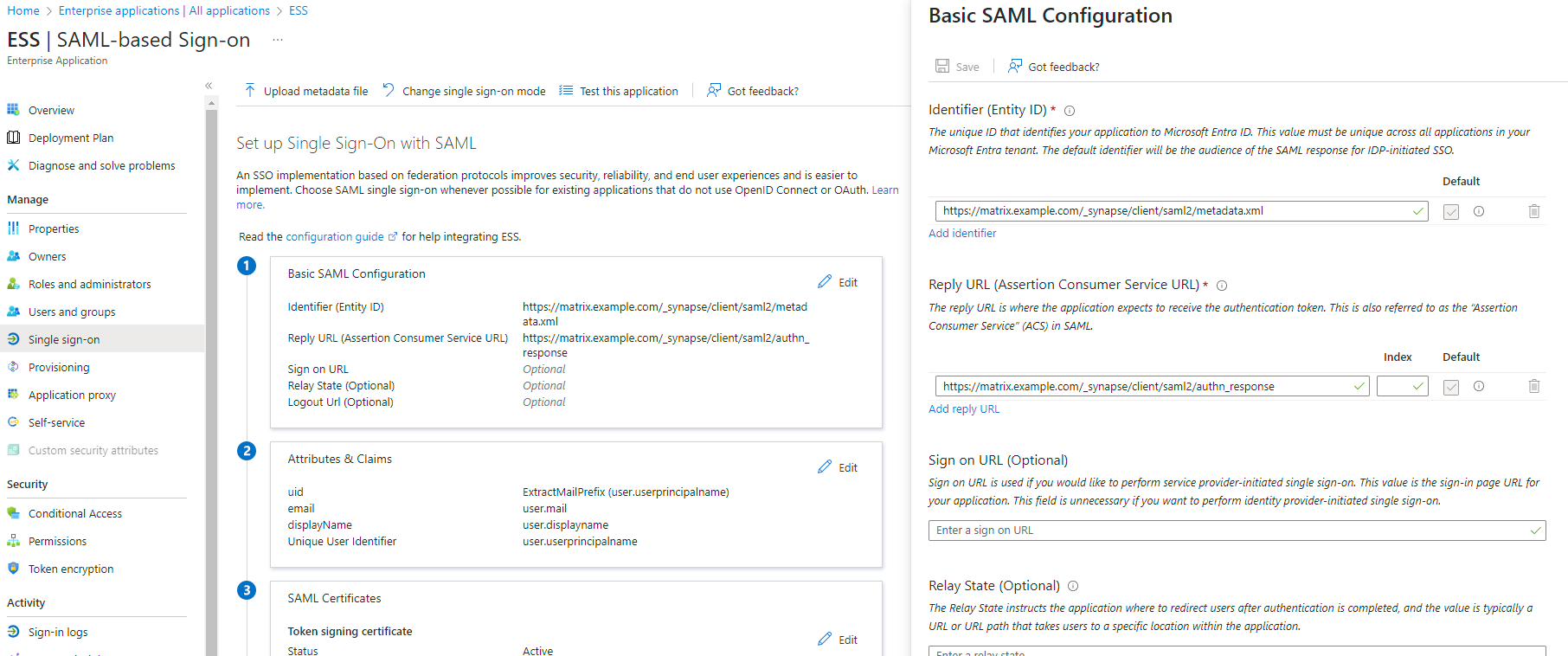
EditonBasic SAML Configuration - In
Identifier, add the following URL :https://<synapse fqdn>/_synapse/client/saml2/metadata.xml - Remove the default URL
- In
Reply URL, add the following URL :https://<synapse fqdn>/_synapse/client/saml2/authn_response - Click on
Save
- Make a note of the
App Federation Metadata UrlunderSAML Certificatesas this will be required in a later step. -
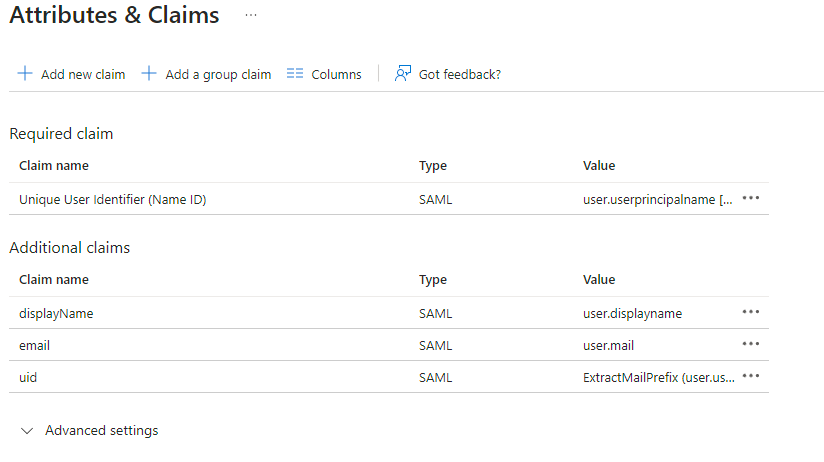
EditonAttributes & Claims - Remove all defaults for additional claims
- Click on
Add new claimto add the following (suggested) claims (the UID will be used as the MXID):- Name:
uid, Transformation :ExtractMailPrefix, Parameter 1 :user.userprincipalname - Name:
email, Source attribute :user.mail - Name:
displayName, Source attribute :user.displayname
- Name:
- Click on
Save
- In the application overview screen select
Users and Groupsand add groups and users which may have access to element
Configure the installer
Add a SAML provider in the 'Synapse' configuration after enabling Delegated Auth and set the following (suggested) fields in the installer:
-
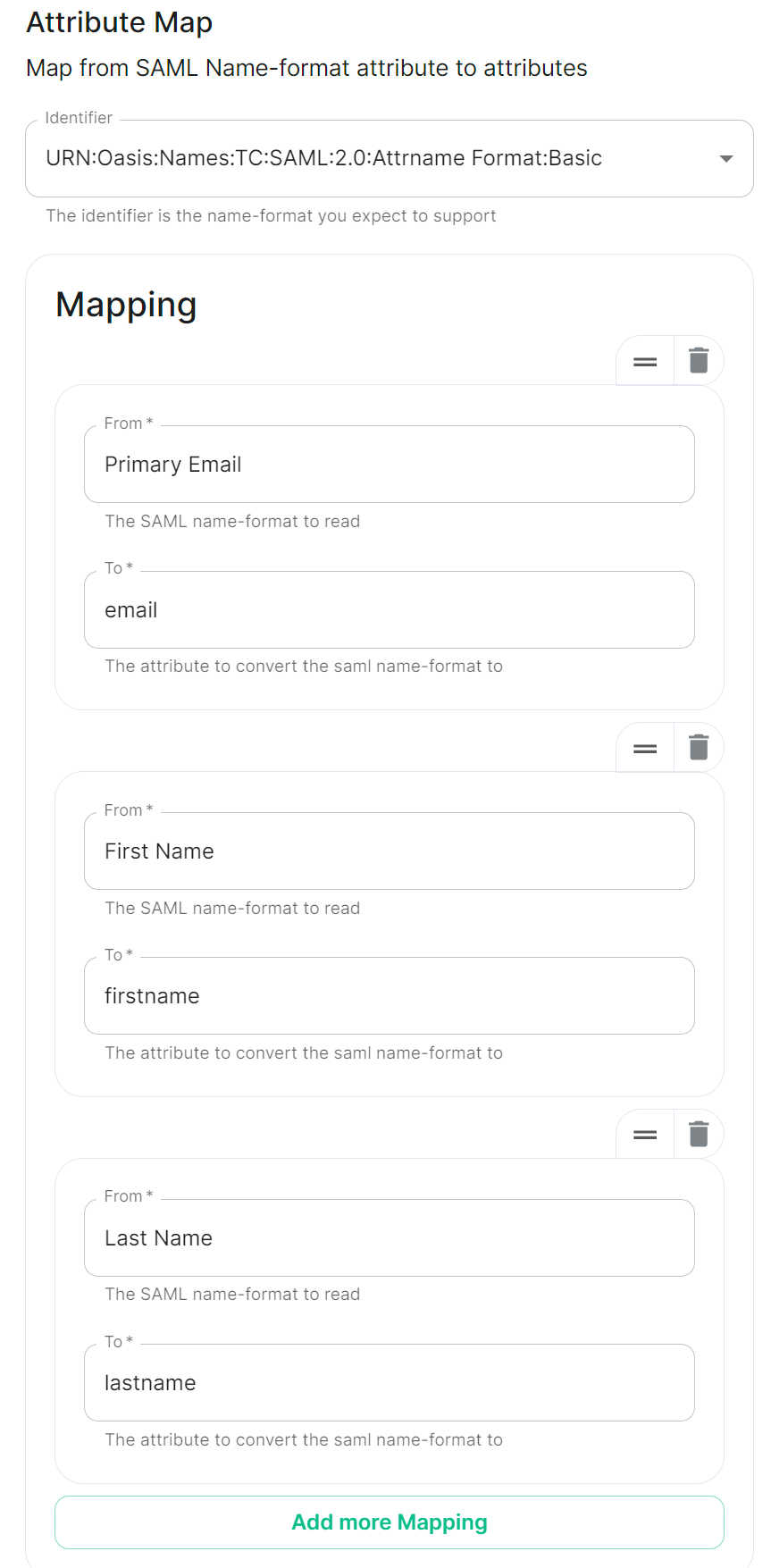
Allow Unknown Attributes - Under
Attribute Map, select theIdentifier-URN:Oasis:Names:TC:SAML:2.0:Attrname Format:Basic
- Under
Mappingadd the following (suggested) mappings:- From:
Primary EmailTo:email - From:
First NameTo:firstname - From:
Last NameTo:lastname
- From:
- Under
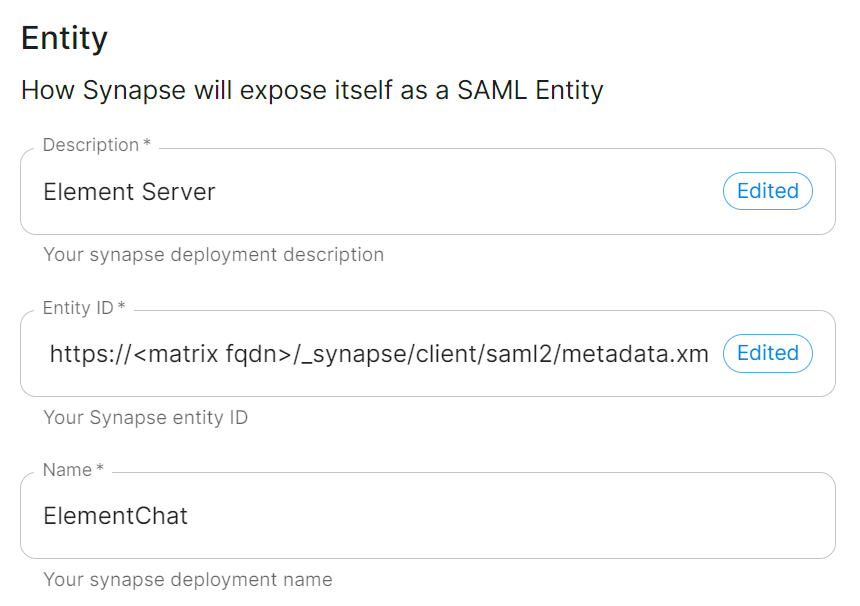
Entity, enter adescription, theEntity ID(from Azure) and aname.
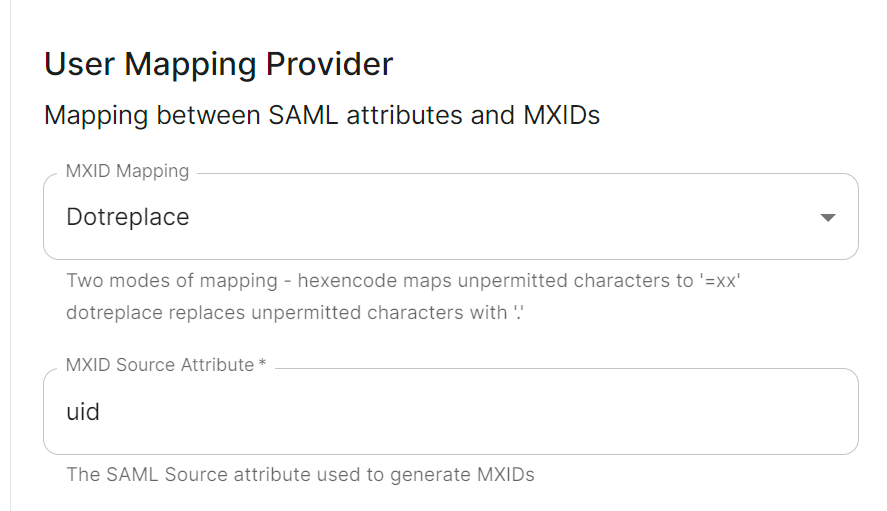
- Under
User Mapping Providerselect the following:-
MXID Mapping:Dotreplace -
MXID Source Attribute:uid
-
- Under
Metadata URL, add theApp Federation Metadata URLfrom Azure.
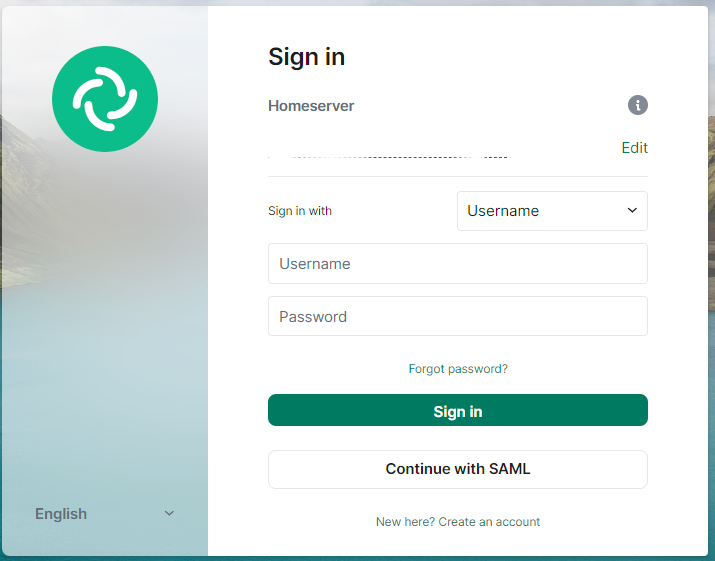
When clients connect, along with any existing authentication methods still enabled, they should now also have an option to Continue with SAML: