Setting up Element Call
Introduction
Element Call is Element's next generation of video calling, set to replace Jitsi in the future. Element Call is currently an experimental feature so please use it accordingly; it is not expected to replace Jitsi yet.
How to set up Element Call
Required domains
In addition to the core set of domains for any ESS deployment, an Element Call installation on ESS uses the following domains:
- Required:
- Element Call Domain: the domain of the Element Call web client.
- Element Call SFU Domain: the domain of the SFU (Selective Forwarding Unit) for forwarding media streams between call participants.
- Optional:
- Coturn Domain: the domain of a Coturn instance hosted by your ESS installation. Required for airgapped environments.
Ensure you have acquired DNS records for these domains before installing Element Call on your ESS instance.
Required ports
Ensure that any firewalls in front of your ESS instance allow external traffic on the following ports:
- Required:
-
443/tcpfor accessing the Element Call web client. -
30881/tcpand30882/udp, for exposing the self-hosted Livekit SFU.
-
- Optional:
-
80/httpfor acquiring LetsEncrypt certificates for Element Call domains. - UDP (and possibly TCP) ports you choose for STUN TURN and/or the UDP relay of a self-hosted Coturn.
-
Basic installation
In the Admin Console, visit the Configure page, select Integrations on the left sidebar, and select Element Call (Experimental).
On the next page, the SFU > Networking section must be configured. Read the descriptions of the available networking modes to decide which is appropriate for your ESS instance.
Next, click the Advanced button at the bottom of the page, then to show the Kubernetes section, then click the Show button in that section.
In the section that appears, configure the Ingress and Ingresses > SFU sections with the Element Call Domain and Element Call SFU Domain (respectively) that you acquired earlier, as well as their TLS sections to associate those domain names with an SSL certificate for secure connections.
Other settings on the page may be left at their defaults, or set to your preference.
How to set up Element Call for airgapped environments
Your ESS instance must host Coturn in order for Element Call to function in airgapped environments. To do this, click Install next to Coturn from the integrations page.
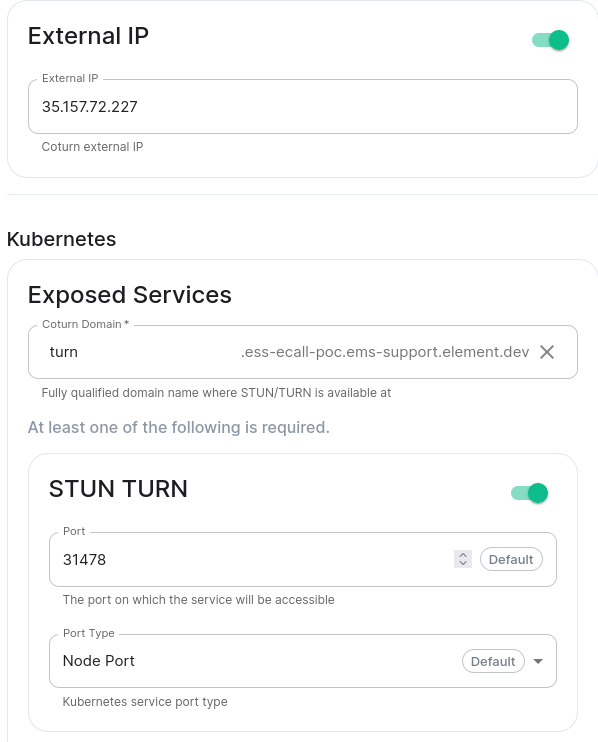
On the Coturn integration page, set the External IP of your ESS instance that clients should be able to reach it at, the Coturn Domain, and at least STUN TURN.
Then, within the Element Call integration page, ensure SFU Networking has no STUN Servers defined. This will cause the deployed Coturn to be used by connecting users as the STUN server to discover their public IP address.
Element Call with guest access
By default, Element Call shares the same user access restrictions as the Synapse homeserver. This means that unless Synapse has been configured to allow guest users, calls on Element Call are accessible only to Matrix users registered on the Synapse homeserver. However, enabling guest users in Synapse to allow unregistered access to Element Call opens up the entire homeserver to guest account creation, which may be undesirable.
To solve the needs of allowing guest access to Element Call while blocking guest account creation on the homeserver, it is possible to grant guess access via federation with an additional dedicated homeserver, managed by an additional ESS instance. This involves a total of two ESS instances:
- The main instance: an existing fully-featured ESS instance where registered accounts are homed & all integrations, including Element Call, are installed. Has Synapse configured with closed or restricted registration.
- The guest instance: an additional ESS instance used only to host guest accounts, and to provide its own deployment of Element Call for unregistered/guest access. Has Synapse configured with open registration.
Guest access to Element Call is achieved via a closed federation between the two instances: the main instance federates with the guest instance and any other homeservers it wishes to federate with, and the guest homeserver federates only with the main instance. This allows unregistered users to join Element Call on the main instance by creating an account on the guest instance with open registration, while preventing these guest accounts from being used to reach any other homeservers.
How to set up Element Call with guest access
- Install Element Call on your existing ESS instance by following the prior instructions on this page. This will be your main instance.
- Prepare another ESS instance, then follow the prior instructions to install Element Call on it. This will be your guest instance.
- In the admin console of each instance:
- In
Synapse > Advanced > Additional, add this YAML content:
experimental_features: msc3266_enabled: true - In
- In the admin console of the main instance:
- In
Element Web > Advanced > Additional configuration, add this JSON content:
{ "features": { "feature_ask_to_join": true }, "element_call": { "guest_spa_url": "https://<guest-instance-element-call-domain>" } }- To limit federation to only the guest instance, apply these settings in the
Synapsesection:- Set
Profile > Federation TypetoLimited - Set
Advanced > Federation > Allow Listto include the the guest instance's Synapse Domain
- Set
- In
- In the admin console of the guest instance:
- To limit federation to only the main instance, apply these settings in the
Synapsesection:- Set
Profile > Federation TypetoLimited - Set
Advanced > Federation > Allow Listto include the main instance's Synapse Domain
- Set
- In
Integrations > Element Call > Additional configuration, add this JSON content:
{ "livekit": { "livekit_service_url": "https://<main-instance-sfu-domain>" } } - To limit federation to only the main instance, apply these settings in the