Authentication Section
A detailed look at Delegated Authentication options available and setup examples.
This is a new section introduced in LTS 24.10 which replaces the previous Delegated Authentication options found within the Synapse section. Your previous configuration will be upgraded on first-run of the newer LTS.
In the Authentication section you will find options to configure settings specific to Authentication. Regardless of if you are using the Matrix Authentication Server, or have enabled Legacy Auth, the settings on this page will remain the same.
However please note, MAS does not support delegated authentication with SAML or GroupSync - if you wish to enable either of these you will need to return to the Host section and enable Legacy Auth.
All settings configured via the UI in this section will be saved to your deployment.yml, with the contents of secrets being saved to secrets.yml. You will find specific configuration examples in each section.
Config Example
-
deployment.ymlmetadata: annotations: ui.element.io/layer: | components: synapse: spec: components: synapse: config: delegatedAuth: -
secrets.ymlkind: Secret metadata: name: synapse namespace: element-onprem data:
By default, if you do not change any settings on this page, defaults will be added to your configuration file/s (see example below).
Config Example
-
deployment.ymlmetadata: annotations: ui.element.io/layer: | components: spec: synapse: config: delegatedAuth: localPasswordDatabase: enableRegistration: false # Note, if you deploy without any authentication methods enabled, the installer will default to Local Accounts. -
secrets.ymlapiVersion: v1 kind: Secret metadata: data: ldapBindPassword: examplePassword
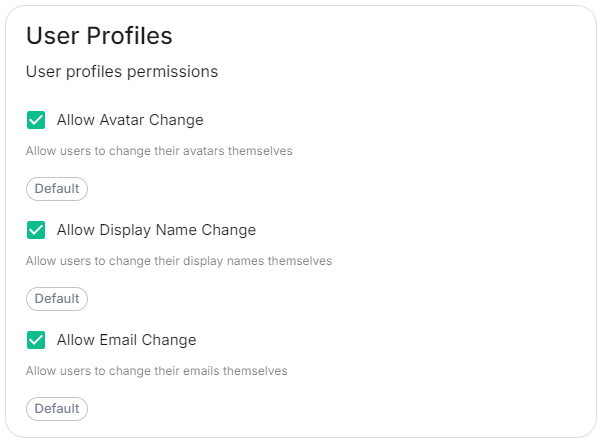
User Profiles
Config Example
spec:
components:
synapse:
config:
delegatedAuth:
userProfiles:
allowAvatarChange: true # Not present if left as default
allowDisplayNameChange: true # Not present if left as default
allowEmailChange: true # Not present if left as default
Self-The User Profiles section provides some self-explanatory config options to adjust whetherwhat changes users are allowed to make changes to their User Profile
such
Atas present,changing wetheir supportDisplay delegatingName. You may wish to restrict this if you'd prefer to delegate the authenticationsetting of usersthese values to the followingassociated Identity Provider.
OIDC
You can add and configure one, or multiple, OIDC providers - to do so you will need to click the Add OIDC / Add more OIDC button found after toggling on the ODIC section:
Once an OIDC provider interfaces:
LDAPSAMLOIDC
When enabling Delegated Auth,added, you can stillremove allowany local users managedproviders by Elementclicking tothe connectrubbish bin icon found to the instance
When Allow Local Users Login is Enabled, you can both connect to your instance using your IDP andof the local database.
Different options are offered by the installer and you can combine two or more options on the same instance like enabling SAML and OIDC delegated authentication.
See the below relevant sections to your environment for specifics on getting configured.provider.
LDAPConfig on Windows AD
Example
spec:
components:
synapse:
config:
delegatedAuth:
oidc:
-
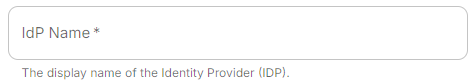
IdP Name
Config Example
spec:
components:
synapse:
config:
delegatedAuth:
oidc:
idpName: example_name # Required
IdP ID
Config
spec:
components:
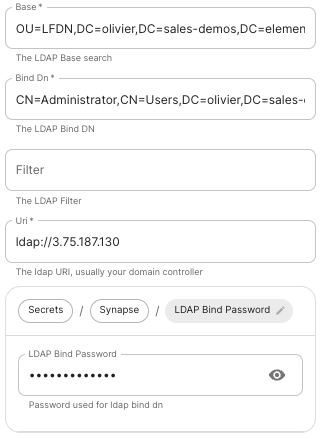
Base.
Thesynapse:
distinguishedconfig:
namedelegatedAuth:
ofoidc:
theidpId: root01JDS2WKNYTQS21GFAKM9AKD9R level# OrgRequired
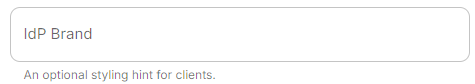
Unit IdP LDAPBrand
TheConfig
distinguishedExamplenamespec:cancomponents:besynapse:displayedconfig:bydelegatedAuth:selectingoidc: idpBrand: example_brand
Issuer
Config Example
Viewspec:
components:
synapse:
config:
delegatedAuth:
oidc:
issuer: https://issuer.example.com/ # Required
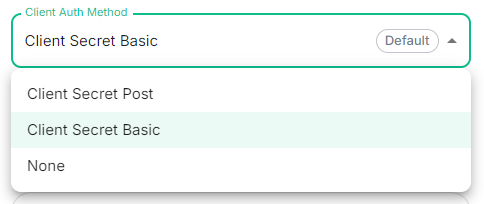
Client Auth Method
Config Example
components:Advancedspec:Featuresinsynapse:theconfig:ActivedelegatedAuth:Directoryoidc:consoleclientAuthMethod:andclient_secret_basicthen,#right-clickingIfonnothe`clientAuthMethod`object,defined,selectingwillProperties/Attributes Editor.
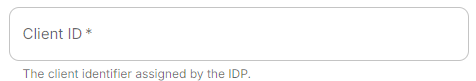
Client URIID
Config serverExample
ldap://dc.example.comspec: components: synapse: config: delegatedAuth: oidc: clientId: example_client_id.
Client isSecret
Config Controller, can also pass in ldaps:// for SSL connectivity.
-
ldap://ServerName:389deployment.ymlspec: components: synapse: config: delegatedAuth: oidc: clientSecretSecretKey: oidcClientSecret -
ldaps://ServerName:636secrets.yml
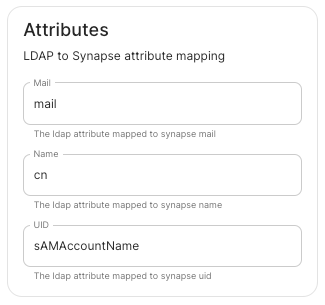
Mail.mailName.cnUID.sAMAccountName
OpenID on Microsoft Azure
Before configuring within the installer, you have to configure Microsoft Azure Active Directory.
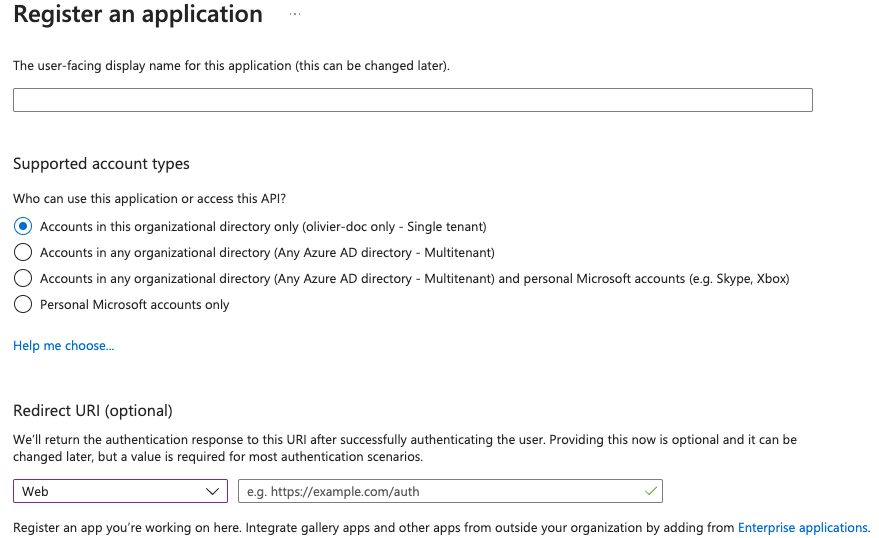
Set up Microsoft Azure Active Directory
You need to create anApp registration.You have to selectRedirect URI (optional)and set it to the following, wherematrixis the subdomain of Synapse andexample.comis your base domain as configured on the Domains section:https://matrix.example.com/_synapse/client/oidc/callbackapiVersion: v1 kind: Secret metadata: name: synapse namespace: element-onprem data: oidcClientSecret: U2VjdXJlT0lEQ0NsaWVudFNlY3JldA==
Allow Existing Users
Config Example
spec:
components:
synapse:
config:
delegatedAuth:
oidc:
Scopes
For the bridge to be able to operate correctly, navigate to API permissions, add Microsoft Graph APIs, choose Delegated Permissions and add: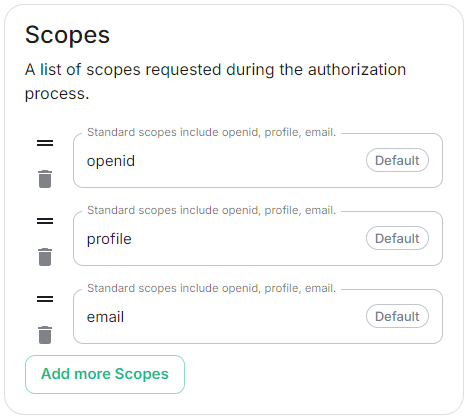
Config Example
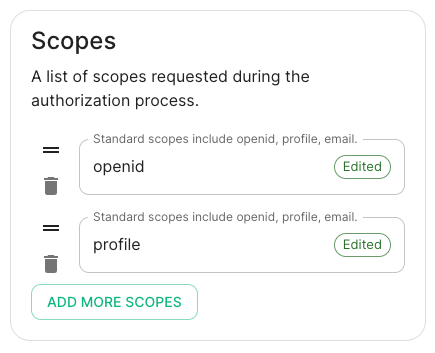
spec: components: synapse: config: delegatedAuth: oidc: scopes: - openid - profile - emailprofileemail
Remember to grant the admin consent for those.
To setup the installer, you'll need:
TheApplication (client) IDTheDirectory (tenant) IDA secret generated fromCertificates & Secretson the app.
Configure the installer
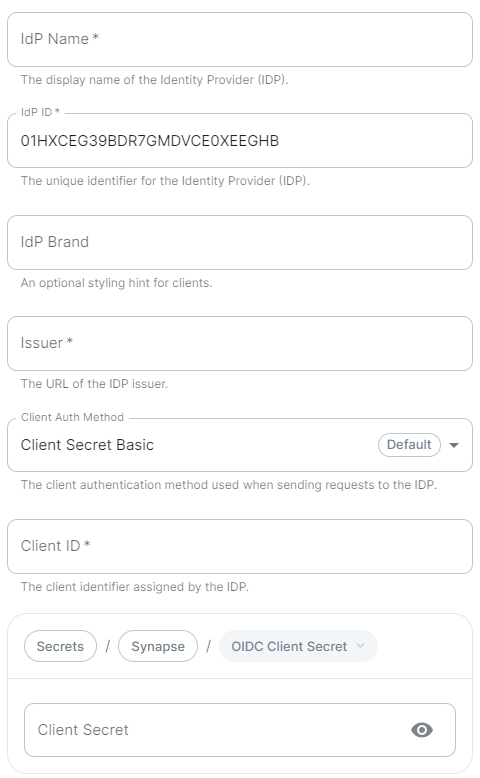 | 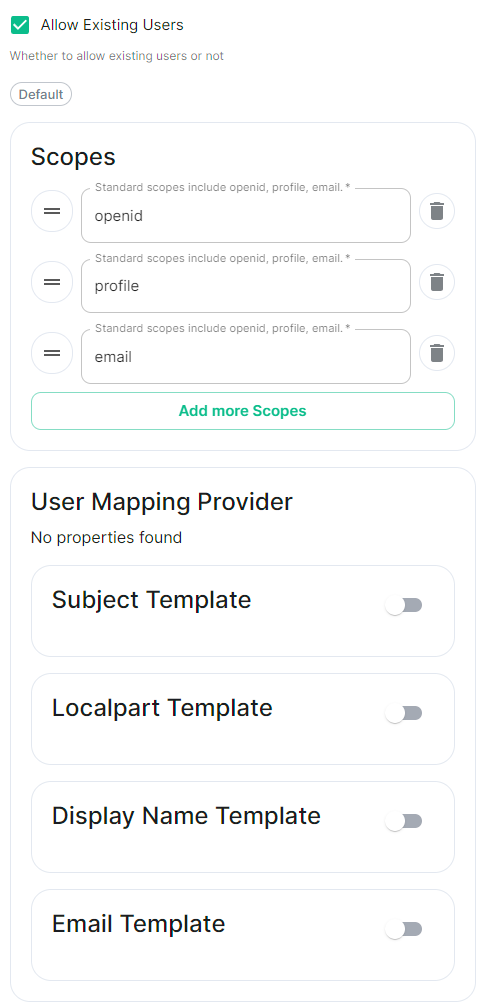 | 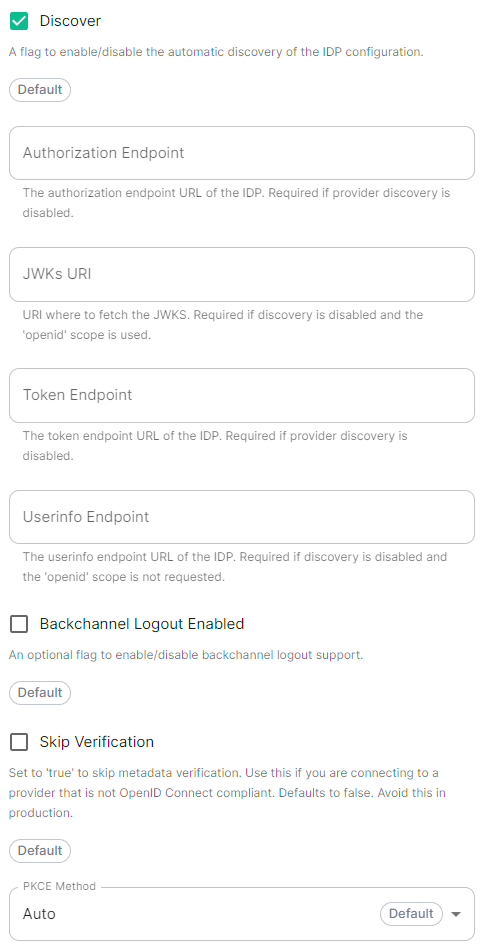 |
IdP Name.A user-facing name for this identity provider, which is used to offer the user a choice of login mechanisms in the Element UI.IdP ID.A string identifying your identity provider in your configuration, this will be auto-generated for you (but can be changed).IdP Brand.An optional brand for this identity provider, allowing clients to style the login flow according to the identity provider in question.Issuer.The OIDC issuer. Used to validate tokens and (if discovery is enabled) to discover the provider's endpoints. Usehttps://login.microsoftonline.com/DIRECTORY_TENNANT_ID/v2.0replacingDIRECTORY_TENNANT_ID.Client Auth Method.Auth method to use when exchanging the token. Set it toClient Secret Postor any method supported by your IdP.Client ID.Set this to yourApplication (client) ID.Client Secret.Set this to the secret value defined under "Certificates and secrets".Scopes.By defaultopenid,profileandemailare added, you shouldn't need to modify these..ConfigurationforhowConfig
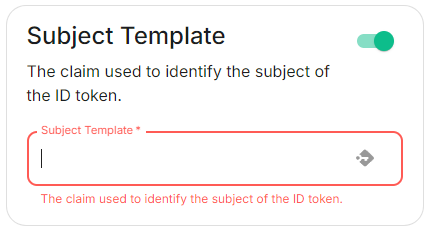
attributesExamplereturnedspec:fromcomponents:asynapse:OIDCconfig:providerdelegatedAuth:areoidc:mappeduserMappingProvider:ontoamatrix user.LocalpartSubject Template
.Jinja2templatefortheConfig
localpartExampleofspec:thecomponents:MXID.Setsynapse:itconfig:todelegatedAuth:oidc: userMappingProvider: subjectTemplate: '{{ user.preferred_username.split('@')[0]subject }}'.-
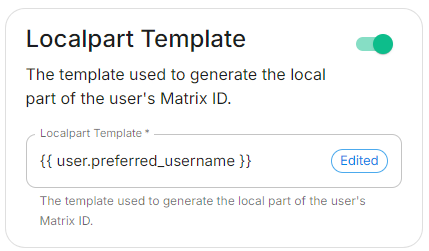
Localpart Template
Config Example
spec: components: synapse: config: delegatedAuth: oidc: userMappingProvider: localpartTemplate: '{{ user.preferred_username }}'Display Name Template
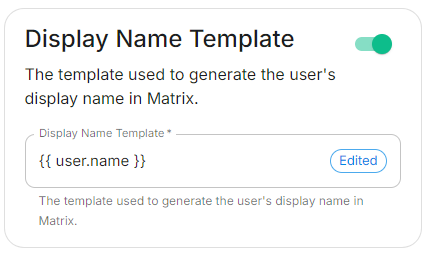
.Jinja2templatefortheConfig
displayExamplenamespec:tocomponents:setsynapse:onconfig:firstdelegatedAuth:login.Ifoidc:unset,userMappingProvider:nodisplayNameTemplate:display name will be set. Set it to'{{ user.name }}'.
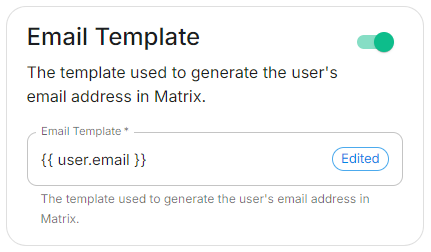
- Template
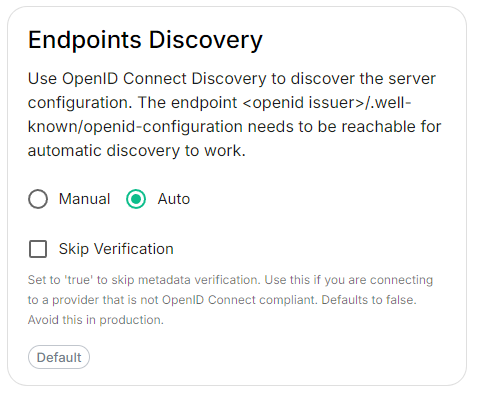
Discover.EnableConfig Example
spec: components: synapse: config: delegatedAuth: oidc: userMappingProvider: emailTemplate: '{{ user.email }}'Endpoints Discovery
Auto Discovery
Config Example
spec: components: synapse: config: delegatedAuth: oidc: - clientId: synapsekieranml clientSecretSecretKey: oidcClientSecret endpointsDiscovery: skipVerification: false idpId: 01JDS2WKNYTQS21GFAKM9AKD9R idpName: Keycloak issuer: https://keycloak.ems-support.element.dev/realms/matrixDisablescopes:the-useopenidof-theprofileOIDC-discoveryemailmechanismuserMappingProvider:todisplayNameTemplate:discover'{{endpoints.user.name - }}'
emailTemplate: '{{ user.email }}'
Skip Verification
Config Example
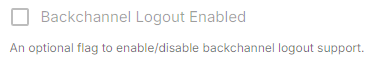
spec: components: synapse: config: delegatedAuth: oidc: - clientId: synapsekieranml clientSecretSecretKey: oidcClientSecret endpointsDiscovery: skipVerification: false idpId: 01JDS2WKNYTQS21GFAKM9AKD9R idpName: Keycloak issuer: https://keycloak.ems-support.element.dev/realms/matrix scopes: - openid - profile - email userMappingProvider: displayNameTemplate: '{{ user.name }}' emailTemplate: '{{ user.email }}'Backchannel Logout Enabled
.Synapse supports receiving OpenID Connect Back-Channel Logout notifications. This lets the OpenID Connect Provider notify Synapse when a user logs out, so that Synapse can end that user session. This property has to bet set tohttps://matrix.example.com/_synapse/client/oidc/backchannel_logoutin your identity provider, wherematrixis the subdomain of Synapse andexample.comis your base domain as configured on the Domains section.
OpenID on Microsoft AD FS
Install Microsoft AD FS
BeforeThe startingMatrix theAuthentication installation,Service makedoes sure:
- support
yourconfiguringWindowsBackchannelcomputerLogout.name is correct since you won't be able to change it after having installed AD FSyou configured your server with a static IP addressyour server joined a domain and your domain is defined under Server Manager > Local serveryou can resolve your server FQDN like computername.my-domain.com
You can findonly aconfigure checklistBackchannel here.
Steps to follow:
Install AD CS (Certificate Server) to issue valid certificates for AD FS. AD CS provides a platform for issuing and managing public key infrastructure [PKI] certificates.Install AD FS (Federation Server)
Install AD CS
You need to install the AD CS Server Role.
Follow thisguide.
Obtain and Configure an SSL Certificate for AD FS
Before installing AD FS, you are required to generate a certificate for your federation service. The SSL certificate is used for securing communications between federation servers and clients.
Follow thisguide.Additionally, thisguideprovides more details on how to create a certificate template.
Install AD FS
You need to install the AD FS Role Service.
Follow thisguide.
Configure the federation service
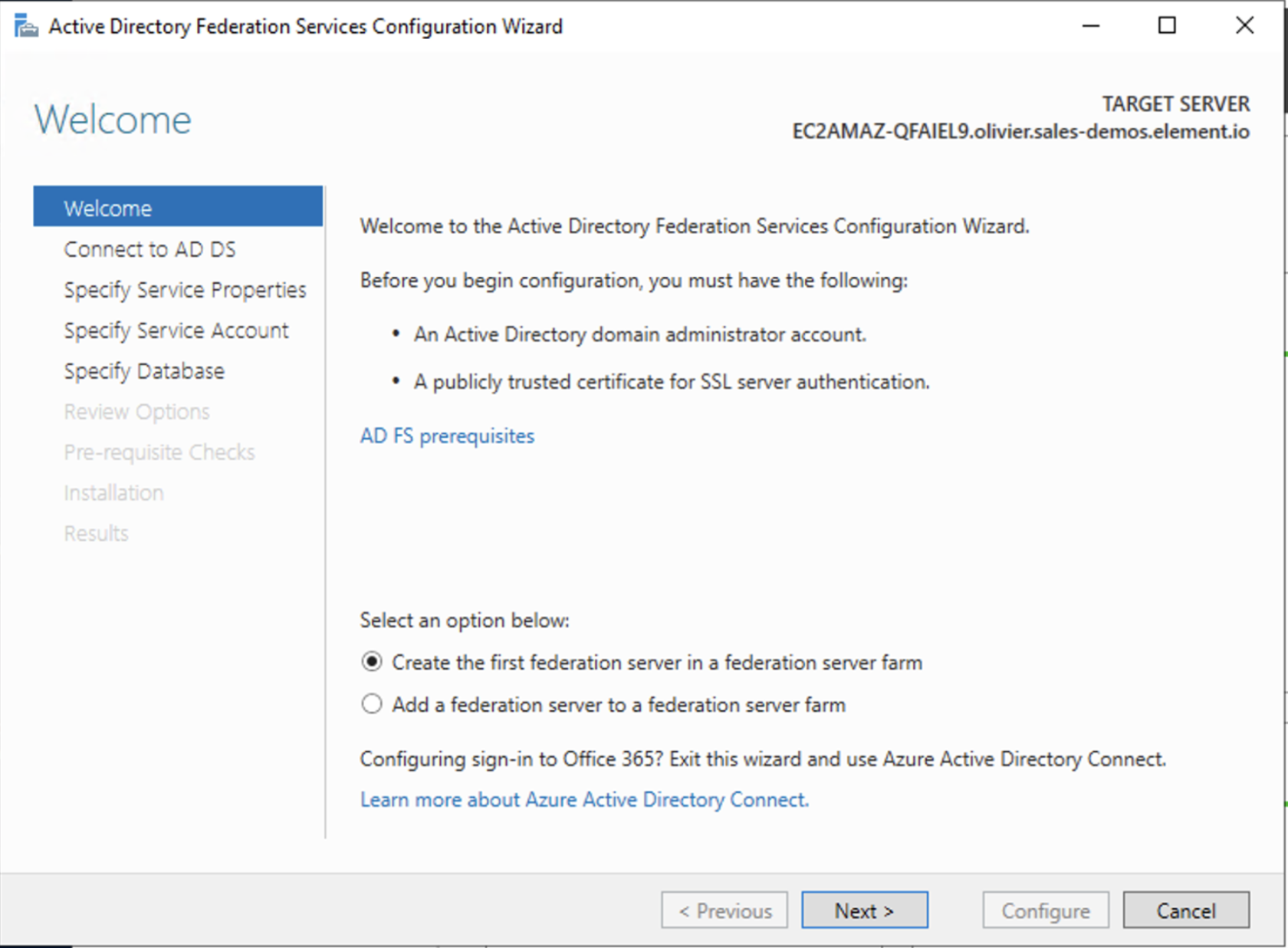
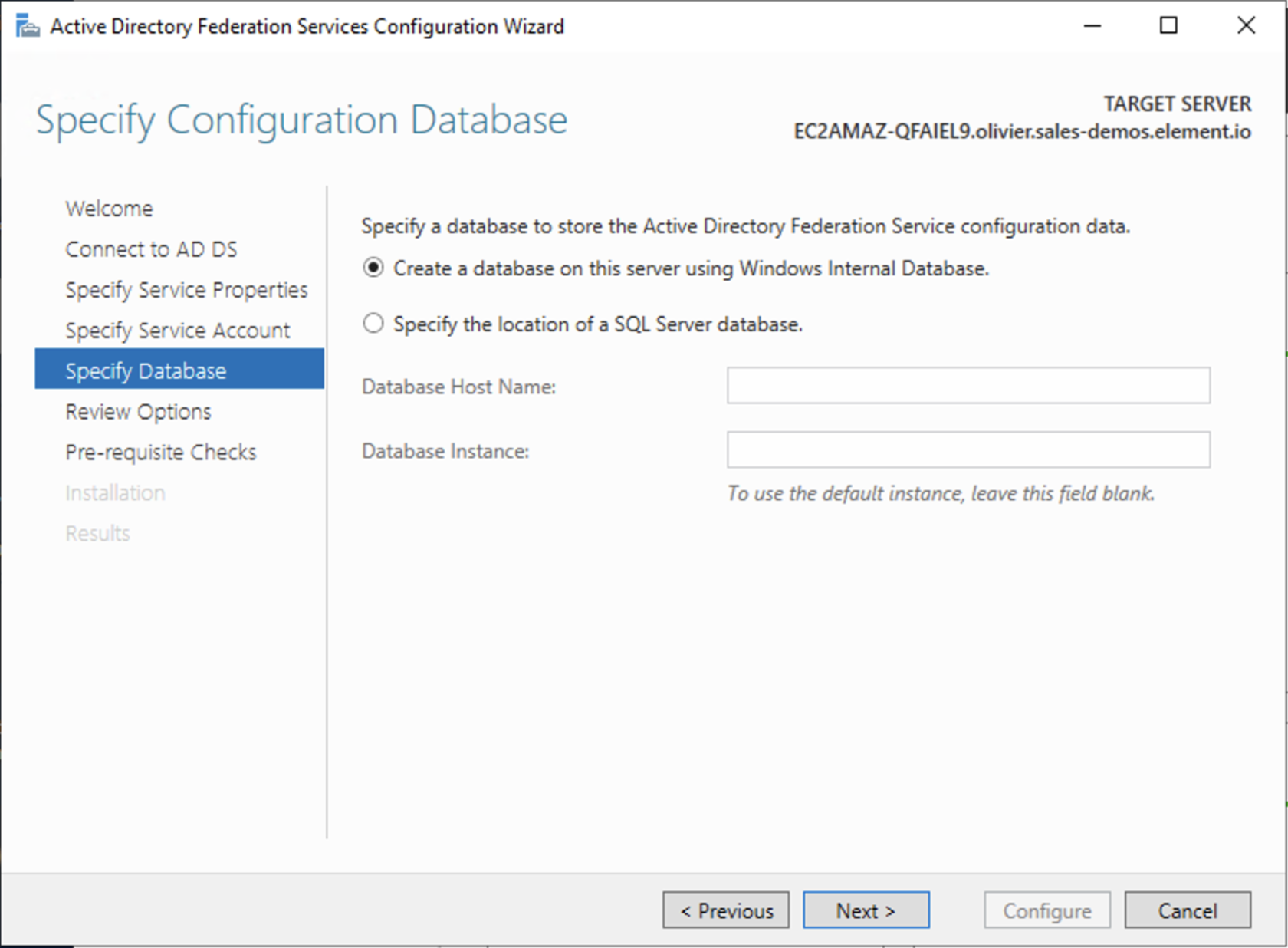
AD FS is installed but not configured.
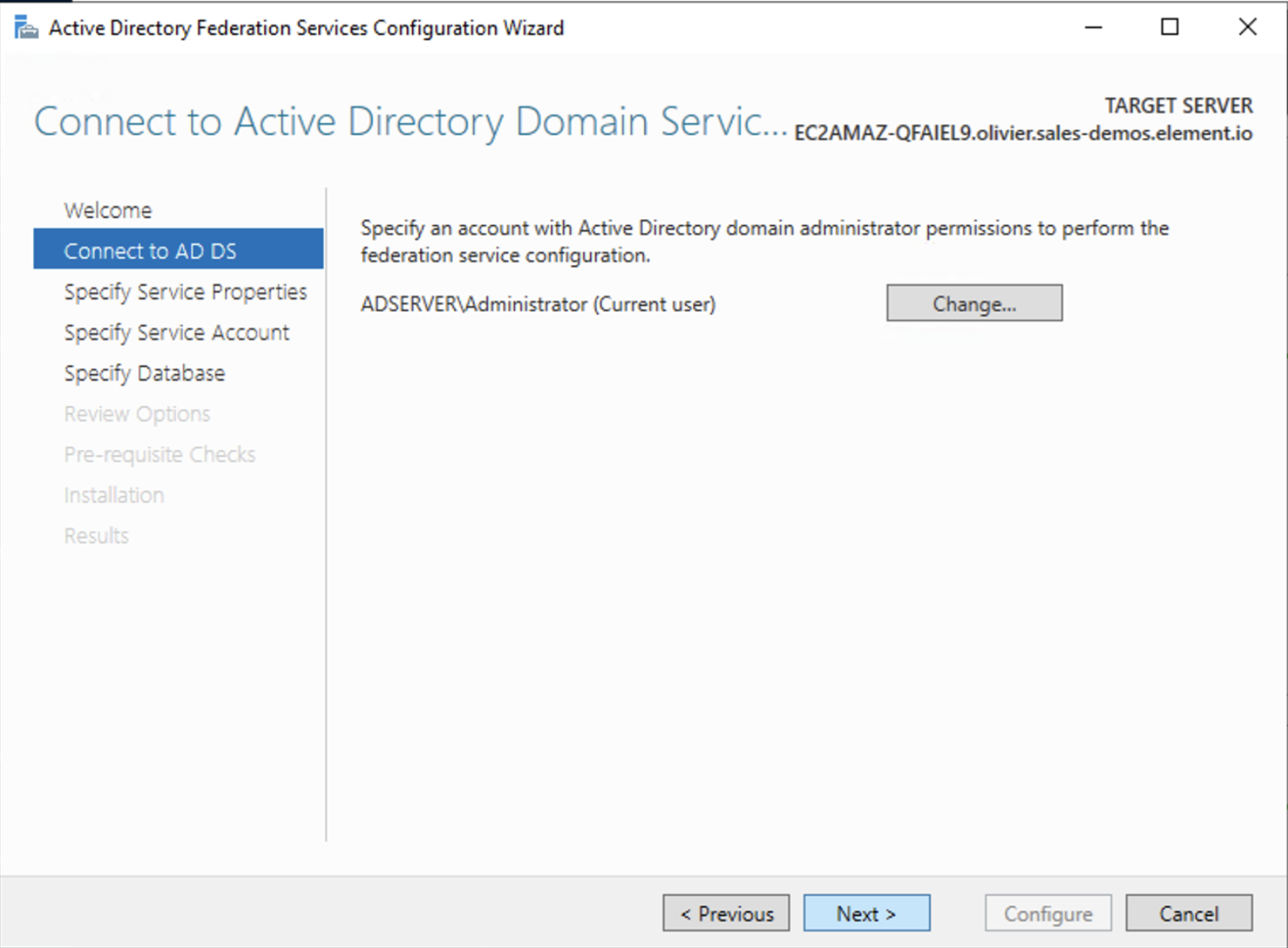
Click onConfigure the federation service on this serverunderPost-deployment configurationin theServer Manager.EnsureCreate the first federation server in a federation server farmand is selected
ClickNext
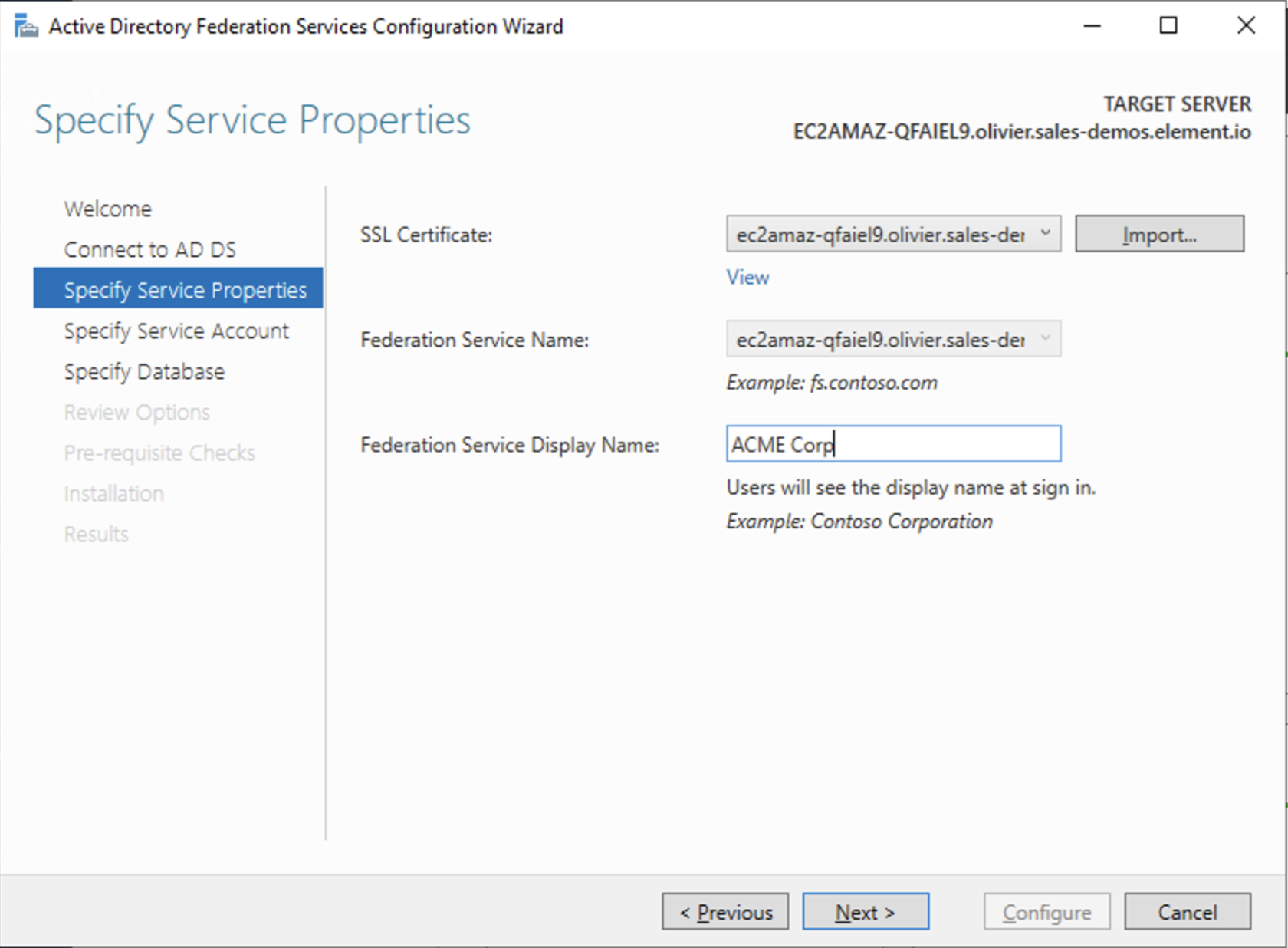
Select the SSL Certificate and set a Federation Service Display Name
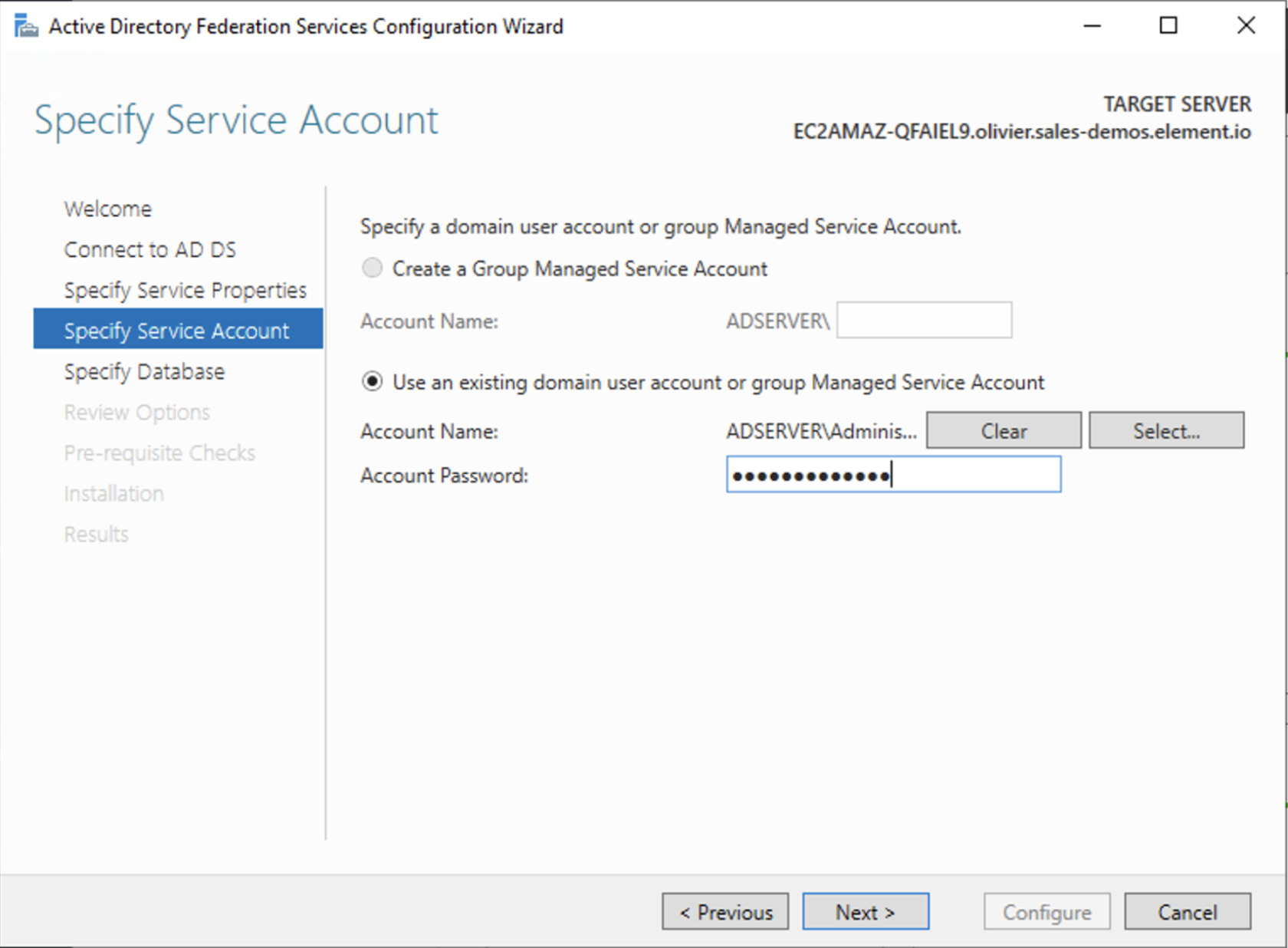
On the Specify Service Account page, you can either Create a Group Managed Service Account (gMSA) or Specify an existing Service or gMSA Account
Choose your database
Review Options , check prerequisites are completed and click onConfigureRestart the server
Add AD FS as an OpenID Connect identity provider
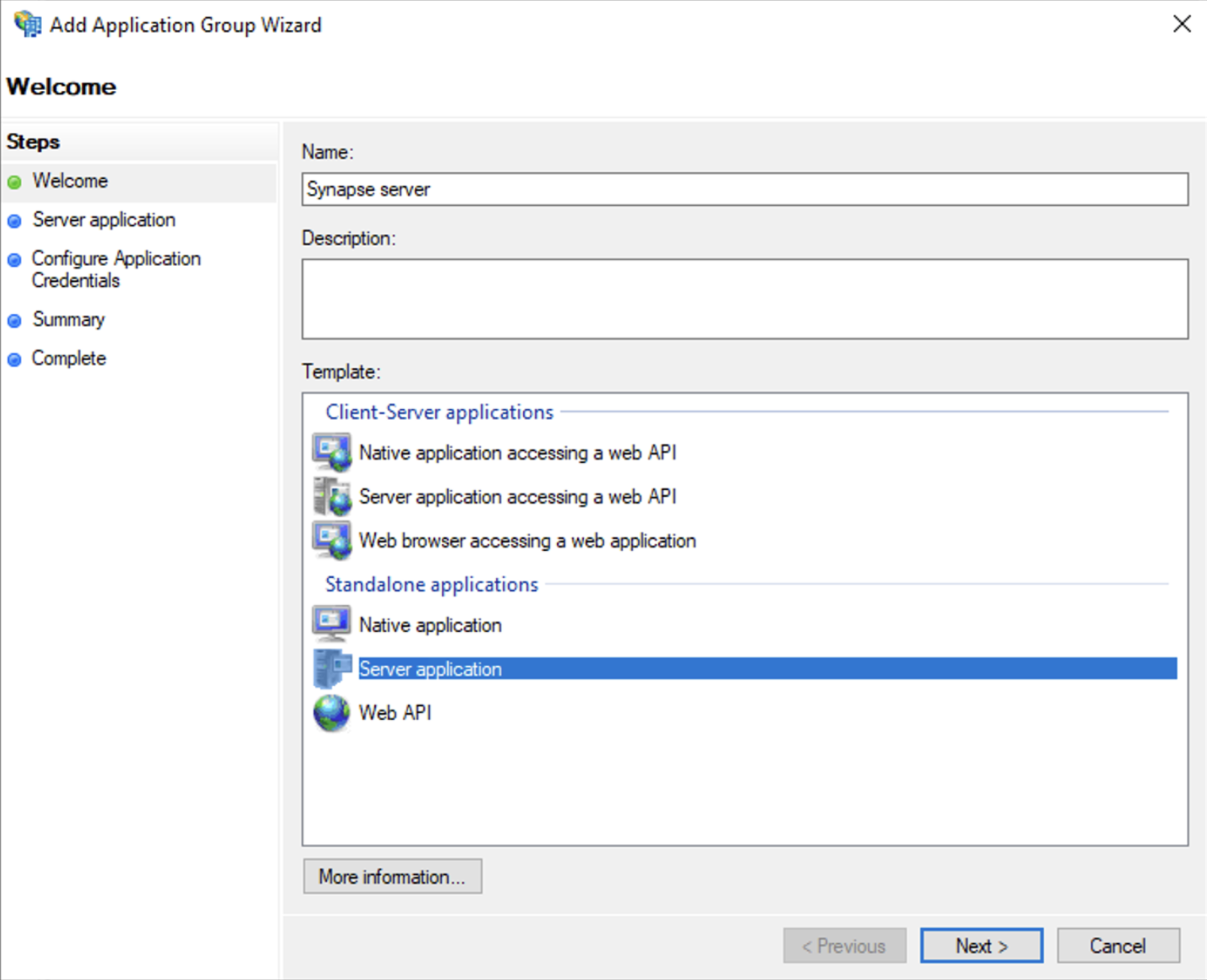
To enable sign-in for users with an AD FS account, create an Application Group in your AD FS.
To create an Application Group, follow theses steps:
InServer Manager, selectTools, and then selectAD FS ManagementIn AD FS Management, right-click onApplication Groupsand selectAdd Application GroupOn the Application Group WizardWelcomescreenEnter the Name of your applicationUnderStandalone applicationssection, selectServer applicationand clickNext
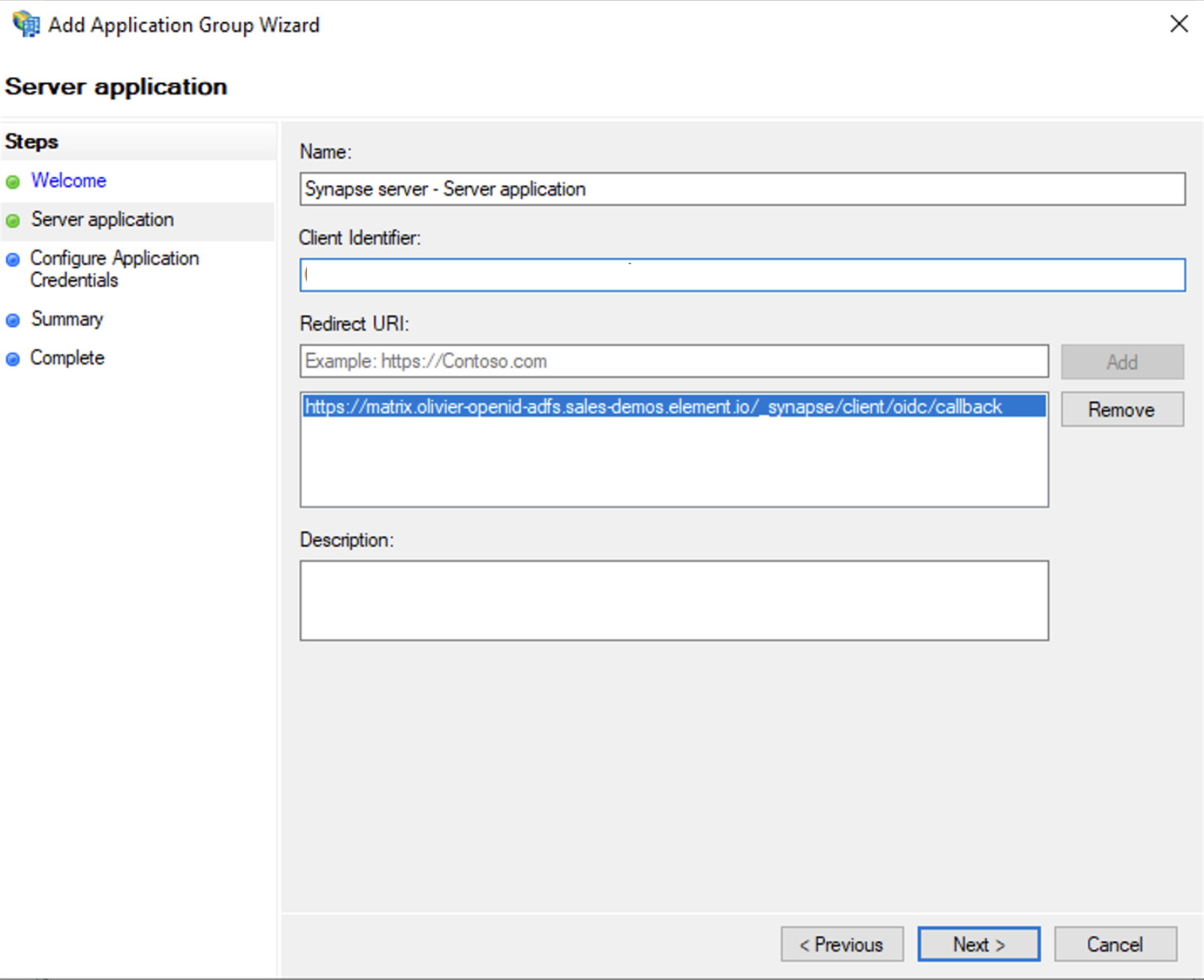
Enterhttps://<matrix domain>/_synapse/client/oidc/callbackin Redirect URI: field, clickAdd, save theClient Identifiersomewhere, you will need it when setting up Element and clickNext(e.g. https://matrix.domain.com/_synapse/client/oidc/callback)
SelectGenerate a shared secretcheckbox and make a note of the generated Secret and pressNext(Secret needs to be added in the Element Installer GUI in a later step)Right click on the created Application Group and select `Properties``
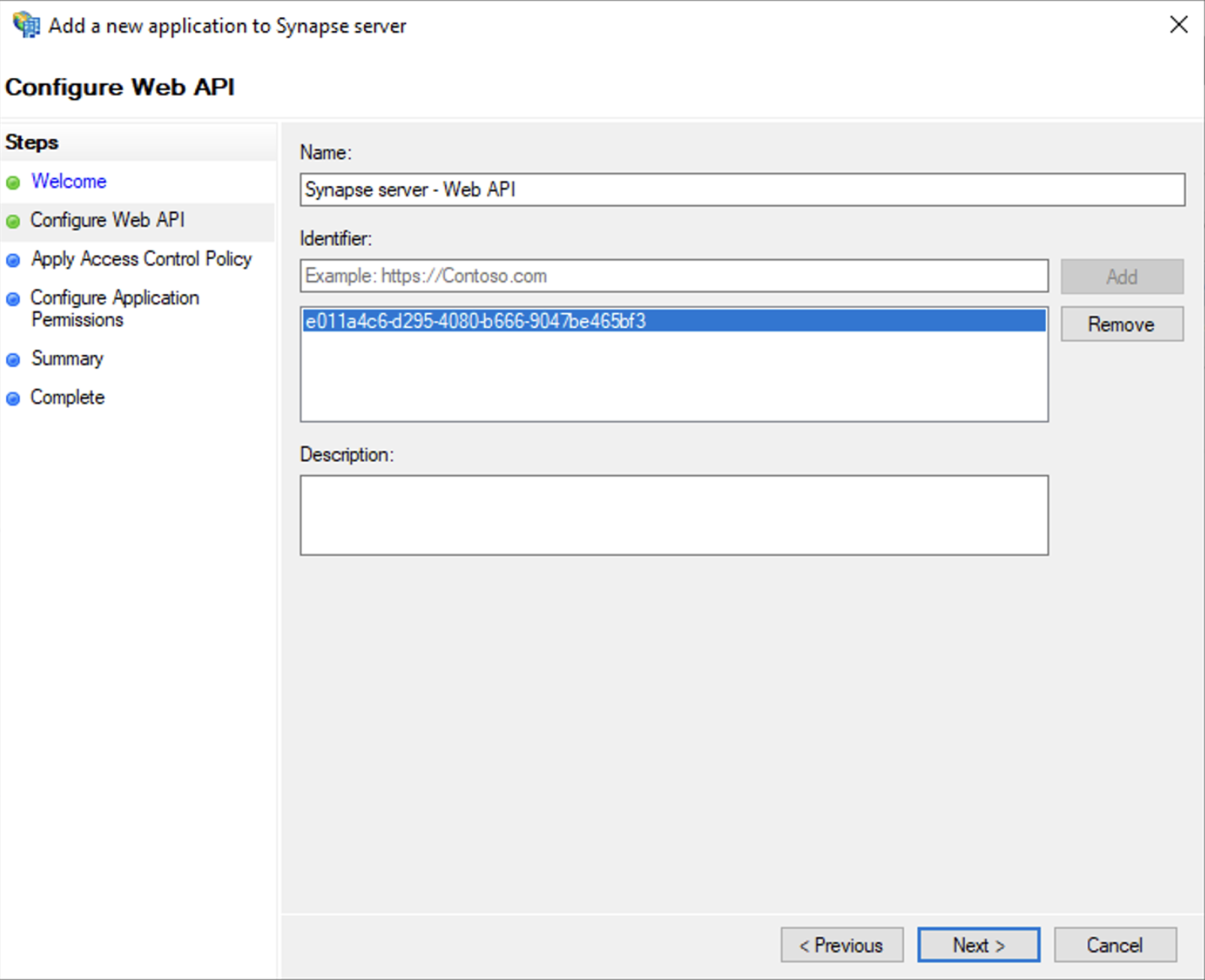
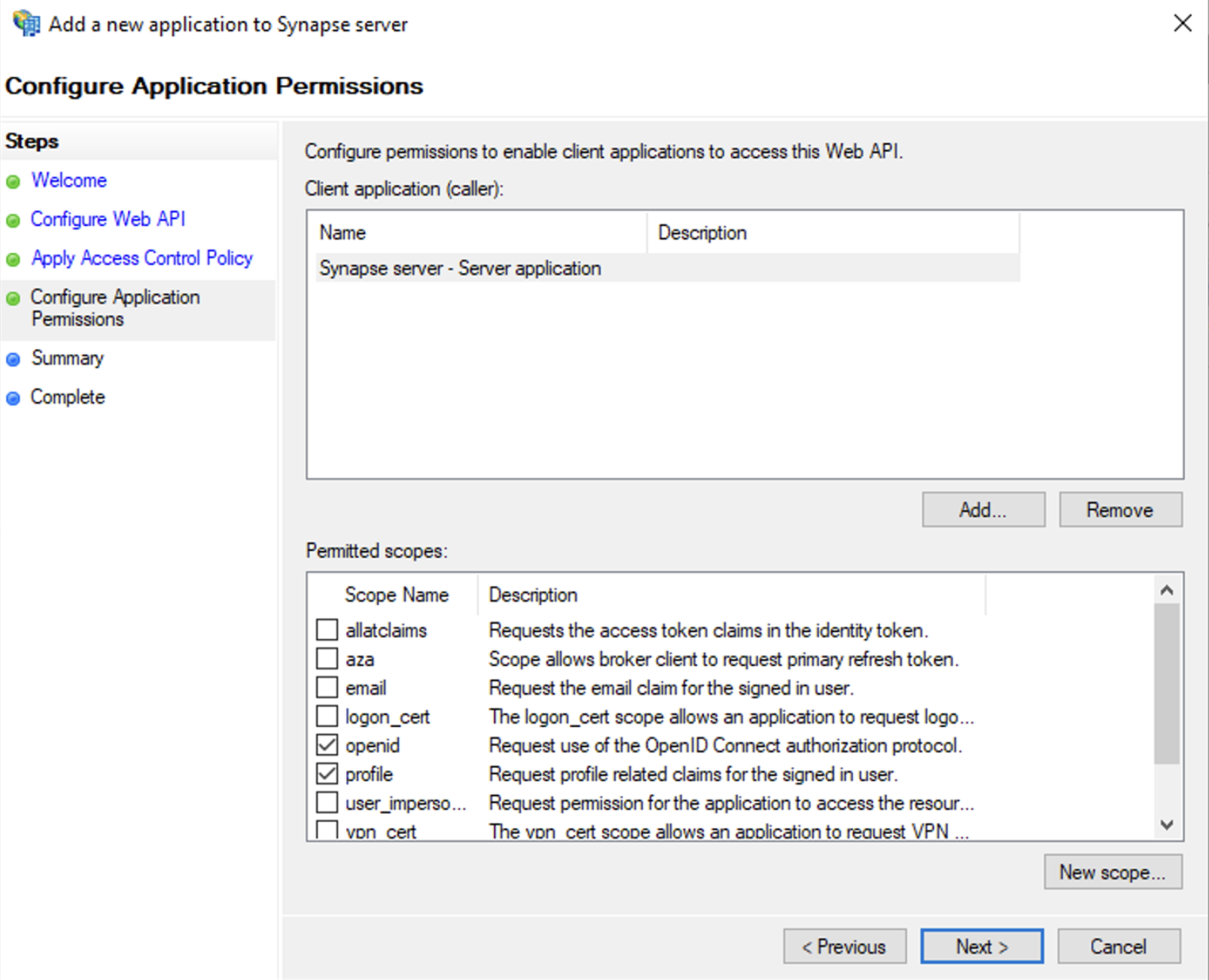
SelectAdd application...button.SelectWeb APIIn theIdentifierfield, type in theclient_idyou saved before and clickNext
SelectPermit everyoneand clickNextUnder Permitted scopes: selectopenidandprofileand clickNext
OnSummarypage, click `Next``ClickCloseand thenOK
Export Domain Trusted Root Certificate
Runmmc.exeAdd theCertificatessnap-inFile/Add snap-in forCertificates,Computer account
UnderTrusted Root Certification Authorities/Certificates, select your DC certRight click and selectAll Tasks/Export...and export asBase-64 encoded X 509 (.CER)Copy file to local machine
Configure the installer
Add an OIDC provider in the 'Synapse' configuration after enabling Delegated Auth and set the following fields in the installer:
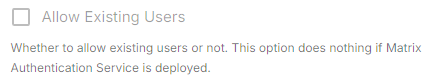
Allow Existing Users:logout ifchecked, it allows a user logging in via OIDC to match a pre-existing account instead of failing. This could be used if switching from password logins to OIDC.Authorization Endpoint: the oauth2 authorization endpoint. Required if provider discovery is disabled.https://login.microsoftonline.com/<Directory (tenant) ID>/oauth2/v2.0/authorizeBackchannel Logout Enabled: Synapse supports receiving OpenID Connect Back-Channel Logout notifications. This lets the OpenID Connect Provider notify Synapse when a user logs out, so that Synapse can end that user session.Client Auth Method: auth method to use when exchanging the token. Set it toClient Secret Basicor any method supported by your IdpClient ID: theClient IDyou saved beforeDiscover: enable/disable the use of the OIDC discovery mechanism to discover endpointsIdp Brand: an optional brand for this identity provider, allowing clients to style the login flow according to the identity provider in questionIdp ID: a string identifying your identity provider in your configurationIdp Name: A user-facing name for this identity provider, which is used to offer the user a choice of login mechanisms in the Element UI. In the screenshot bellow,Idp Nameis set toAzure AD
Issuer: the OIDC issuer. Used to validate tokens and (if discovery is enabled) to discover the provider's endpointshttps://<your-adfs.domain.com>/adfs/Token Endpoint: the oauth2 authorization endpoint. Required if provider discovery is disabled.Client Secret: your client secret you saved before.Scopes: add every scope on a different lineThe openid scope is required which translates to the Sign you in permission in the consent UIYou might also include other scopes in this request for requesting consent.
User Mapping Provider: Configuration for how attributes returned from a OIDC provider are mapped onto a matrix user.Localpart Template: Jinja2 template for the localpart of the MXID. Set it to{{ user.upn.split('@')[0] }}for AD FS
Other configurations are documented here.
SAML on Microsoft Azure
Before setting up the installer, you have toenabled configureLegacy MicrosoftAuthEntrafrom ID.the Host Section.
Set
Config EntraExample
spec:
components:
synapse:
config:
delegatedAuth:
oidc:
- clientId: synapsekieranml
clientSecretSecretKey: oidcClientSecret
endpointsDiscovery:
skipVerification: false
idpId: 01JDS2WKNYTQS21GFAKM9AKD9R
idpName: Keycloak
issuer: https://keycloak.ems-support.element.dev/realms/matrix
scopes:
- openid
- profile
- email
userMappingProvider:
displayNameTemplate: '{{ user.name }}'
emailTemplate: '{{ user.email }}'
SAML
WithThe anMatrix accountAuthentication withService enoughdoes rights,not gosupport SAML and it is recommended to :switch to OIDC. You can only enable SAML authentication if you have enabled EnterpriseLegacy ApplicationsAuth
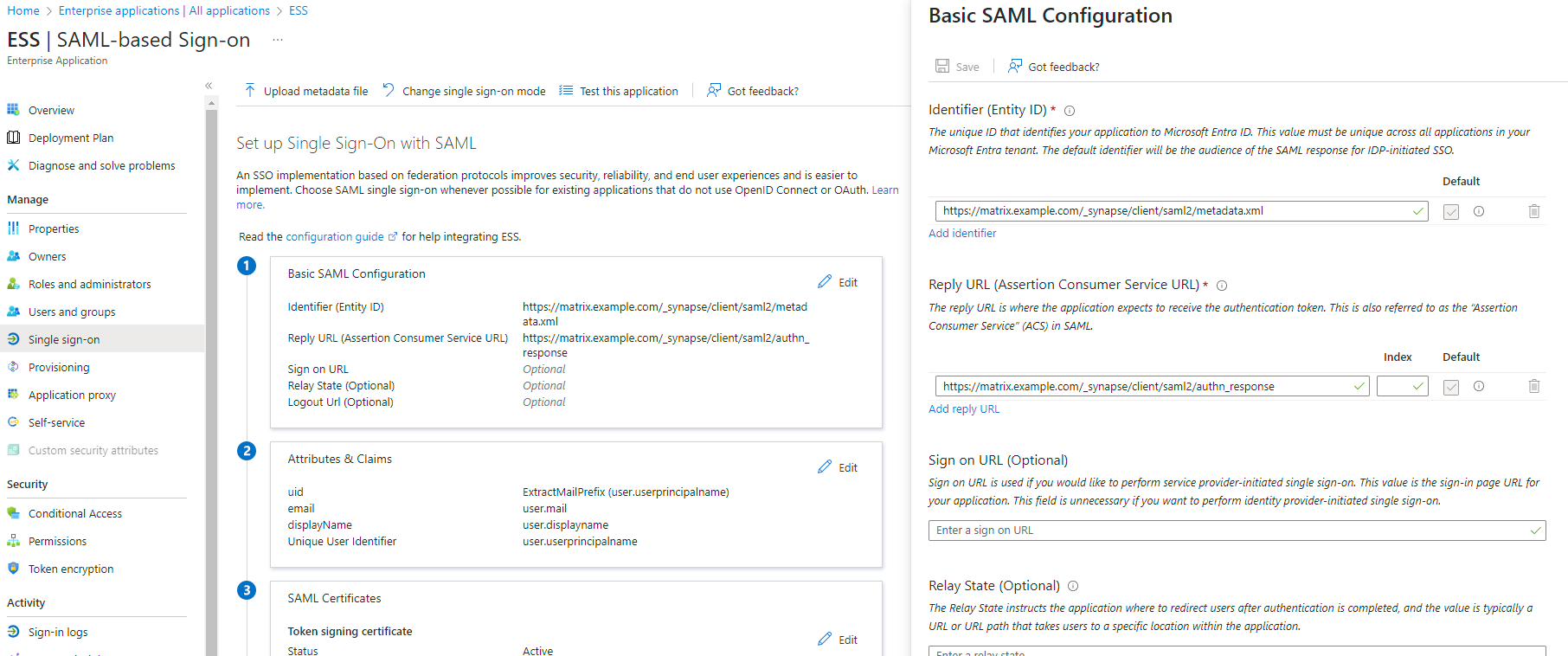
Click onNew ApplicationClick onCreate your own applicationonfrom thetopHostleft cornerChoose a name for it, and selectIntegrate any other application you don't find in the galleryClick on "Create"SelectSet up single sign onSelectSAMLEditonBasic SAML ConfigurationInIdentifier, add the following URL :https://synapse_fqdn/_synapse/client/saml2/metadata.xmlRemove the default URLInReply URL, add the following URL :https://synapse_fqdn/_synapse/client/saml2/authn_responseClick onSave
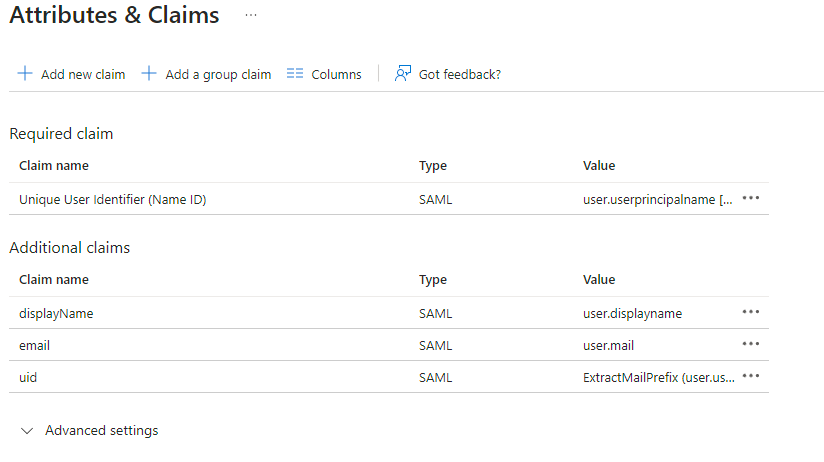
Make a note of theApp Federation Metadata UrlunderSAML Certificatesas this will be required in a later step.EditonAttributes & ClaimsRemove all defaults for additional claimsClick onAdd new claimto add the following (suggested) claims (the UID will be used as the MXID):Name:uid, Transformation :ExtractMailPrefix, Parameter 1 :user.userprincipalnameName:email, Source attribute :user.mailName:displayName, Source attribute :user.displayname
Click onSave
In the application overview screen selectUsers and Groupsand add groups and users which may have access to element
Configure the installer
Add a SAML provider in the 'Synapse' configuration after enabling Delegated Auth and set the following (suggested) fields in the installer:
Allow Unknown Attributes.CheckedAttribute Map.SelectURN:Oasis:Names:TC:SAML:2.0:Attrname Format:Basicas theIdentifierMapping.Set the following mappings:From:Primary EmailTo:emailFrom:First NameTo:firstnameFrom:Last NameTo:lastname
Entity.Description.Entity ID.(From Azure)Name.
User Mapping Provider.Set the following:MXID Mapping:DotreplaceMXID Source Attribute:uid
Metadata URL.Add theApp Federation Metadata URLfrom Azure.
LDAP
TroubleshootingLocal Accounts
Redirection loop on SSO
Synapse needs to have the X-Forwarded-For and X-Forwarded-Proto headers set by the reverse proxy doing the TLS termination. If you are using a Kubernetes installation with your own reverse proxy terminating TLS, please make sure that the appropriate headers are set.