Setting up Group Sync with the Installer
What is Group Sync?
Group Sync allows you to use the ACLs from your identity infrastructure in order to set up permissions on Spaces and Rooms in the Element Ecosystem. Please note that the initial version we are providing only supports a single node, non-federated configuration.
Note: This documentation is presently out of date. We will be working to update this in the near future. Until then, if you have questions about setting up group sync in the installer, please file a support ticket or reach out to your Element representative.
Configuring Group Sync
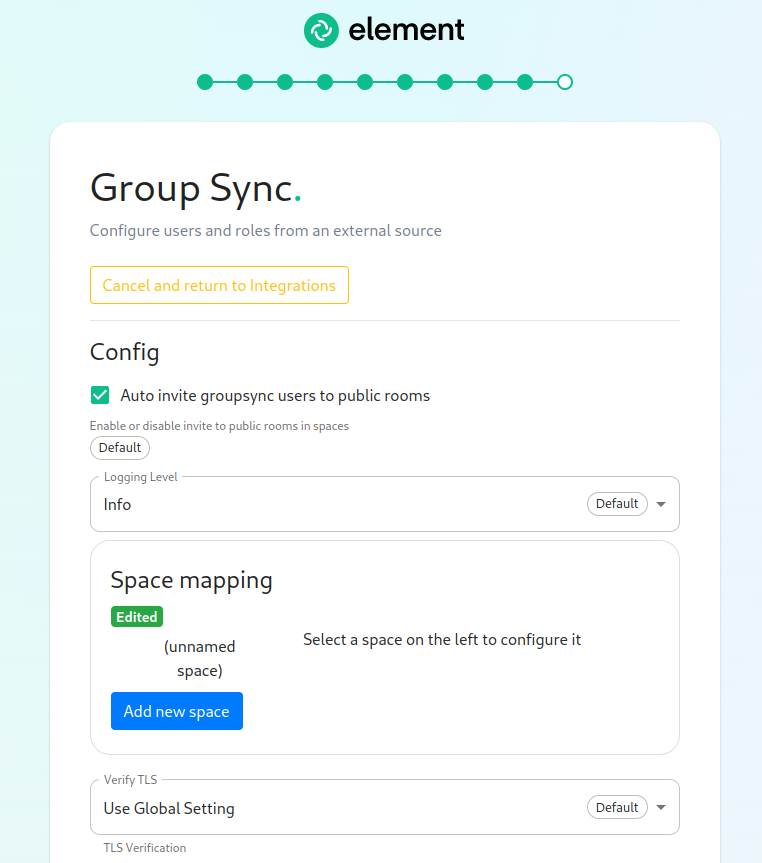
From the Installer's Integrations page, click "Install" under "Group Sync".
Configuring the source
LDAP Servers
- You should create a ldap account with read access to the OUs containing the users
- This account should use password authentication
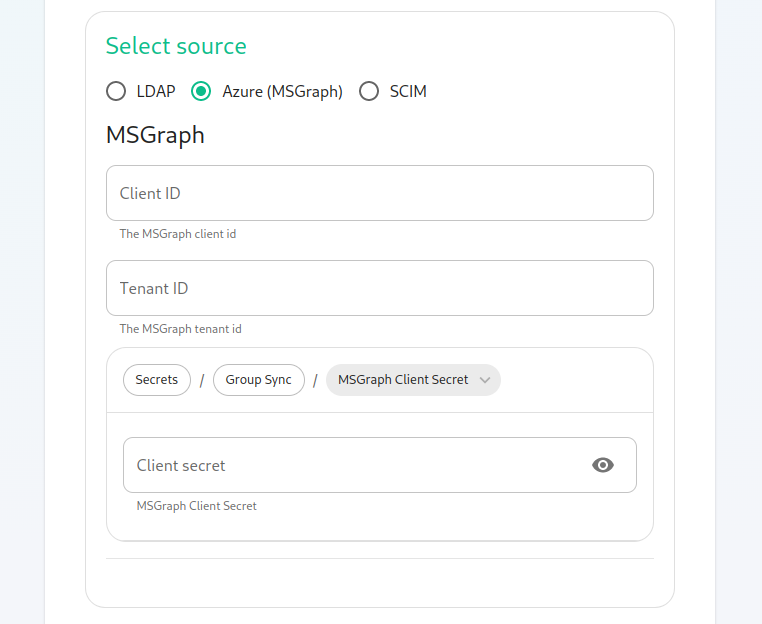
MS Graph (Azure AD)
-
You need to create an
App registration. You'll need theTenant IDof the organization, theApplication (client ID)and a secret generated fromCertificates & secretson the app. -
For the bridge to be able to operate correctly, navigate to API permissions and ensure it has access to Group.Read.All, GroupMember.Read.All and User.Read.All. Ensure that these are Application permissions (rather than Delegated).
-
Remember to grant the admin consent for those.
-
To use MSGraph source, select MSGraph as your source.
-
msgraph_tenant_id: This is the "Tenant ID" from your Azure Active Directory Overview -
msgraph_client_id: Register your app in "App registrations". This will be its "Application (client) ID" -
msgraph_client_secret: Go to "Certificates & secrets", and click on "New client secret". This will be the "Value" of the created secret (not the "Secret ID").
-
Space Mapping
The space mapping mechanism allows us to configure additional spaces that Group Sync will maintain, beyond the ones that it creates by default. It is optional – the configuration can be skipped if no additional spaces are to be created.
This is especially useful when used with bridges other than LDAP, which would normally not create any spaces other than the company-wide one. When used with the LDAP backend, the spaces created from LDAP OrgUnits will be added to the list of subspaces of the toplevel space.
Space mapping also replaces the group power level configuration and group filtering, being a superset of their functionality. It is recommended to use space mapping in their instead, as they might eventually be deprecated and removed.
The interface provided gives you a graphical way to do this.